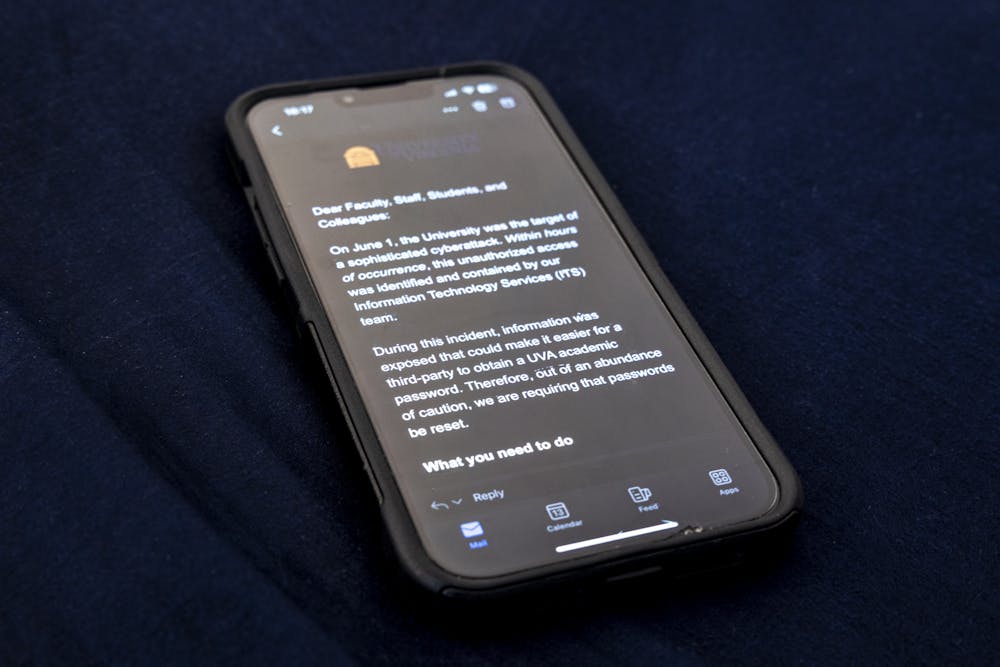
The University required students and faculty to reset their academic passwords by 9 a.m. Wednesday morning or risk losing access to their accounts as a precaution after the University was the target of a cyberattack June 1, according to an email sent to those affected.
In the email, J.J. Davis, executive vice president and chief operating officer, said that no personally identifiable, financial or health information was accessed during the breach. Davis also said the attack was identified and contained by Information Technology Services within hours of occurrence.
According to the University’s incident response webpage, one part of the encrypted password information that requires an encryption key was exposed, resulting in the need for students and faculty to change their passwords.
The high volume of people attempting to reset their passwords caused the system to be offline for a few hours Tuesday morning. Around 25,000 students were potentially affected by June’s cyberattack.
University spokesperson Brian Coy confirmed that ITS took the password reset system down briefly to perform upgrades after there was an increased load from students and faculty who were trying to update their passwords. He said the upgrades resulted in a smoother user experience.
“Password changes are a precaution to address any potential risks created by this incident,” University spokesperson Brian Coy said in an email statement to the Cavalier Daily.
Computer Science Prof. David Evans said the password reset process was likely more difficult and stressful than the University expected because the password reset system couldn’t deal with the number of requests.
“Maybe that experience will help them if there is another incident like this,” Evans said.
According to the University’s incident response posted on the ITS website, the specific information that was exposed could potentially make it easier for a third-party to obtain an individual’s academic password.
Evans said he is confident in the University’s system and that it was consistent with the best practices — even though he’s not personally involved with the internal system.
“There’s nothing you can do that makes you invulnerable to any attack,” Evans said.
Evans said students’ passwords are never stored directly, but instead an encrypted version of the password created by an algorithm is stored. He also said that the University has good reason to require password resets because the more time an adversary has with access to the password file, the more time they have to guess the correct password.
The University states on the ITS website that they plan to invest in security measures for its internal information as cyberattacks become more frequent.The website also says they are engaging with third party vendors to assist in investigation and remediation efforts.
Coy said the University is constantly identifying, blocking and responding to potential cyber threats and that they will continue to do so in the future.